Jeremy IT labs did a fantastic job in explaining and detailing what goes on at this stratum of electronic communication, hence, we really recommend looking at his video on this. Also, Practical Networking YouTube video on this topic gave very interesting insights to the topic also.
Everything we are going to discuss here has its foundation in understanding the Transport Layer, also known as Layer 4 of the OSI model. This layer is responsible for the efficient movement of segments and datagrams between end hosts, whether through the reliability of Transmission Control Protocol (TCP) or the speed of User Datagram Protocol (UDP). A solid grasp of these two protocols is essential for both CCNA preparation and real-world troubleshooting. Note that one focuses on reliability while the other focuses on optimised speed.
Layer 4 – The Transport Layer
The transport layer is responsible for maintaining reliable, orderly, and efficient communication between devices. Its core functions includes process-to-process delivery, multiplexing, congestion/flow control and error management, collectively ensure that networked applications operate seamlessly, forming the foundation for dependable enterprise communication systems.
The transport layer plays a critical role in ensuring reliable data transfer within the OSI model. It receives data from the session layer, checks it for errors or corruption, and divides it into smaller segments before passing it to the lower layers for transmission. The two main protocols we get to see in this layer is the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP). It utilises these two protocols to manage how data moves across the network, so long. The transport layer serves as the bridge between the upper-layer applications and the underlying network, ensuring that data is delivered efficiently, correctly, and to the right destination.
End hosts often run multiple services at once. For instance, a server hosting HTTPS website while also managing Active Directory sessions with a domain controller, it may also have security monitoring tools running in them. Layer 4, the Transport Layer, ensures data is reliably transferred between these processes and reaches the right application. Positioned between the Network Layer (IP addressing and routing) and the Application Layer (protocols like HTTP or SSH), it acts as the network’s traffic controller, directing data between communicating programs. This application-to-application or process-to-process delivery is achieved using 16-bit port numbers, which identify the sending and receiving applications to ensure each message reaches its correct destination. When multiple programs or applications are running simultaneously on a device, these port numbers allow the transport layer to distinguish between them and direct the correct data to each process.
This brings about another key function known as multiplexing and demultiplexing. Multiplexing allows multiple applications on the sender’s side to share a single network connection, combining their data streams for transmission. At the receiver’s end, demultiplexing separates these combined streams and delivers each to the appropriate application. This capability enables many network services to function concurrently over the same link without confusion.
Every network application communicates using a unique combination of an IP address and a port number, together known as a socket. This pairing ensures that data reaches the correct program on the correct device. Port numbers are divided into three main ranges. Well-known ports (0–1023) are reserved for core services such as HTTP on port 80, SSH on port 22, and FTP on port 21. Registered ports (1024–49151) are assigned to user applications or specific software vendors, while ephemeral ports (49152–65535) are temporary and randomly chosen by client devices during communication.
For example, when a computer opens a webpage, the connection may use source port 50000 on the client and destination port 80 on the web server. This system allows multiple applications—such as web browsing, file transfers, and DNS lookups—to operate at the same time without interfering with each other, keeping all sessions organized and independent.
The transport layer also manages congestion control, which prevents and mitigates traffic overload on the network. Congestion occurs when too much data is transmitted at once, overwhelming routers and causing delays or packet loss. Open-loop control methods aim to prevent congestion before it happens by regulating traffic flow, while closed-loop control mechanisms detect and resolve congestion once it occurs. This ensures smooth and efficient network performance, particularly in large enterprise environments where data volumes are high.
Another essential function is flow control, which regulates the rate of data transmission between the sender and receiver. It ensures that a fast sender does not overwhelm a slower receiver by sending more data than it can process. This is often implemented through the sliding window protocol, where acknowledgments and window sizes determine how much data can be sent before requiring confirmation.
Finally, error control ensures that data arrives accurately and intact. The transport layer detects and corrects errors using checksums or error-detecting codes. If corrupted data is found, acknowledgment (ACK) and negative acknowledgment (NACK) messages are exchanged between the sender and receiver. These signals help identify lost or damaged segments and trigger retransmission when necessary. Through this mechanism, the transport layer provides end-to-end reliability even over imperfect network connections.
Layer 4 Protocol – Transmission Control Protocol (TCP)
TCP is the backbone of reliable communication. It is connection-oriented, meaning both devices establish a connection before exchanging data. Just like everything layer 4, it lives above IP and below the Application layer, providing dependable, end-to-end delivery between specific processes or application on different hosts. Applications are identified with 16-bit port numbers, so TCP can deliver data to the exact service that needs it.
TCP begins with a formal three-way handshake: the client sends SYN, the server replies SYN-ACK, and the client answers with ACK. Only then does data flow. This set up of this connection just described is the reason why it is described as connection oriented. When either side is finished, the session is torn down cleanly with FIN/ACK exchanges so both hosts agree the conversation is over.
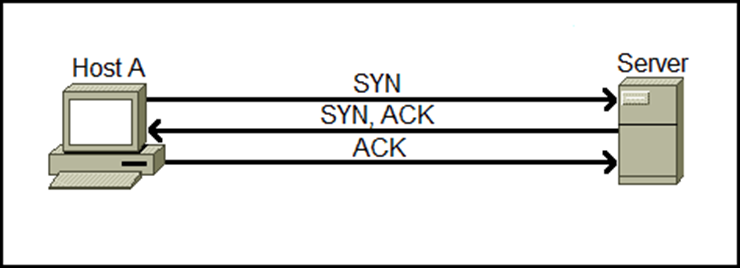
It confirms delivery using acknowledgments. If an expected acknowledgment does not arrive, TCP retransmits the missing data. This makes delivery “informed” rather than magically guaranteed; if the path is broken, TCP can detect loss and try again, but it cannot force delivery over a dead link. Every byte in a TCP stream is numbered. If packets arrive out of order because different network paths have different delays, TCP buffers and reorders them before handing data to the application, ensuring the application sees a clean, in-order stream. This functions with a built-in mechanism that prevents a fast sender from overwhelming a slow receiver using window-based flow control. It also adapts to network conditions with congestion-control algorithms that probe for available bandwidth, back off when loss occurs, and then ramp up again. The result is efficient use of capacity with minimal drops over variable, multi-hop paths.
TCP carries a header, which is at least 20 bytes and up to 60 with options field, containing sequence and acknowledgment numbers, flags (SYN, ACK, FIN, etc.), window size, checksum, and more. The extra fields enable reliability, ordering, and flow control, at the cost of additional per-packet overhead.
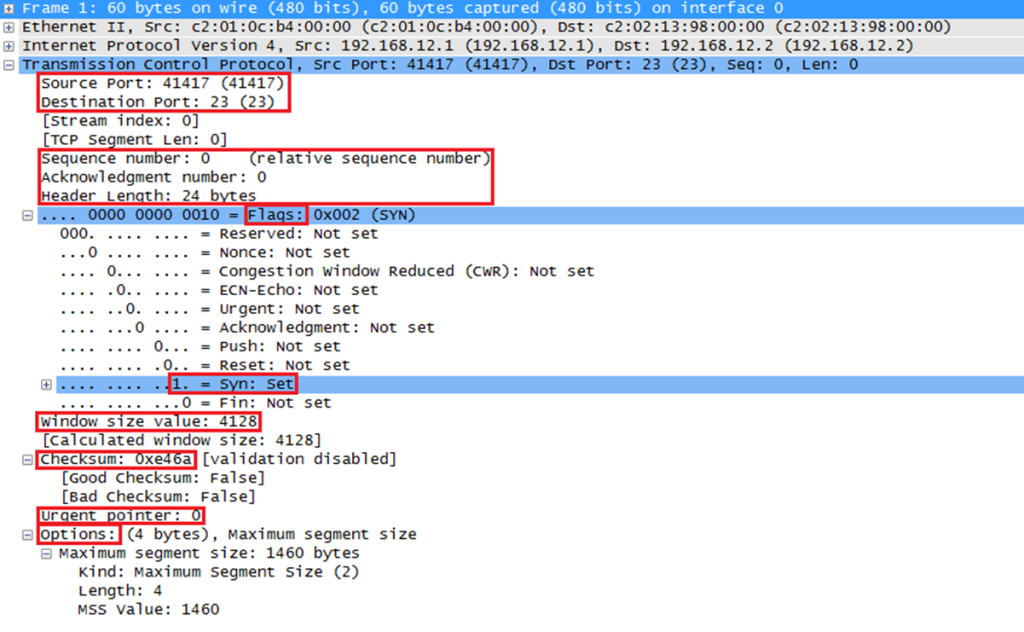
In enterprise environment, because of its reliability and ordered delivery, TCP is preferred for web and API traffic (HTTP/HTTPS), file transfers, email, database replication, and most business applications where correctness matters more than a few extra milliseconds of setup or control traffic. Security is not built into it ordinarily, TCP by itself does not encrypt or authenticate data. Security is added by higher-layer protocols such as TLS (for HTTPS, SMTPS, etc.) or by IPsec below it. Choosing TCP does not inherently make traffic “more secure”; it simply makes delivery reliable.
Layer 4 Protocol – User Datagram Protocol (UDP)
UDP is the connectionless Transport-layer protocol. It also uses IP for routing and 16-bit ports for process addressing, but it does not set up or tear down sessions. Applications send discrete datagrams, and the network delivers them on a best-effort basis. A sender transmits immediately; the receiver processes what arrives. Engineers sometimes speak informally about a “UDP session,” but in practice it is just a group of packets sharing the same five-tuple (source IP/port, destination IP/port, protocol) within a time window.
UDP does not acknowledge receipt and does not retransmit on loss. If an application needs delivery confirmation, it must implement its own logic above UDP. The chance a datagram reaches the other end is governed by the same physical network as TCP; the difference is simply that UDP does not track or recover from loss at Layer 4. It neither sequences packet nor reorders them. If ordering matters, the application must be designed to handle it. UDP also lacks flow and congestion control; it will happily transmit as fast as the sender allows, which is perfect for real-time streams but can cause drops at bottlenecks if the path cannot keep up. Its header is minimal, 8 bytes with just source port, destination port, length, and checksum (often mandatory in IPv6; optional in some IPv4 contexts). The tiny header lowers CPU and bandwidth overhead and reduces per-packet processing delay in network devices.
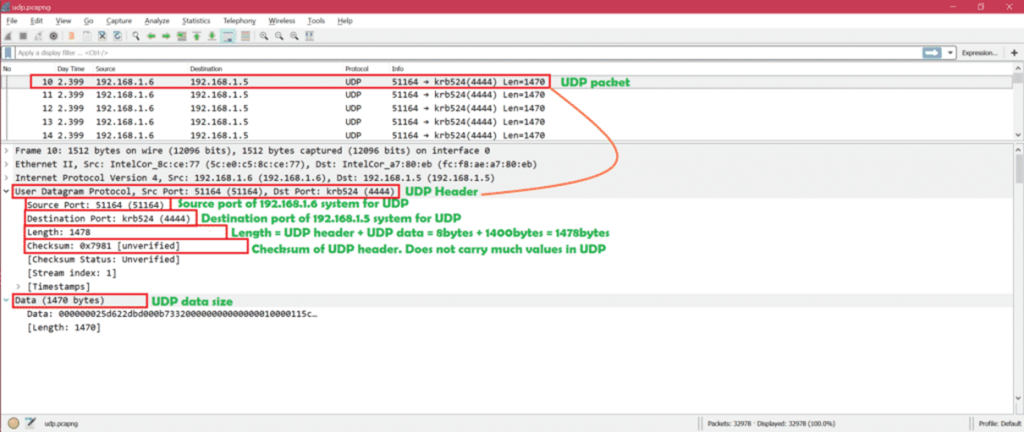
UDP is ideal were time-based efficiency beats perfection. Voice and video (VoIP, conferencing), live streams, gaming telemetric/logging/monitoring applications, simple request/response protocols like DNS, DHCP, SNMP, and syslog often use UDP because occasional loss is acceptable or because the application layer supplies its own reliability. Like TCP, UDP offers no native encryption or authentication. Secure designs pair UDP with protocols such as DTLS or run it within VPNs or IPsec when confidentiality and integrity are required.





